Entanglement Distribution and Routing in Quantum Networks
Secure communication and distributed computing are fundamental to the future of cybersecurity. Quantum networks, built upon the principles of quantum mechanics, enable entanglement-based quantum key distribution (QKD), providing theoretically unbreakable encryption. Beyond QKD, entanglement distribution is crucial for secure distributed quantum computing, allowing multiple quantum processors to work together securely across a network. Additionally, robust entanglement distribution supports blind quantum computing, where a client can outsource quantum computations to a remote server while preserving data privacy, and enhances quantum-enhanced sensing, which improves measurement precision in distributed quantum systems.
At CEROC, we are pioneering novel approaches to entanglement distribution and routing to enhance the security and efficiency of quantum networks. Some of our recent contributions include:
- Entanglement Routing in a Space–Air–Ground Quantum (SPARQ) Network: We developed SPARQ, a quantum network that integrates space, aerial, and ground
nodes for seamless on-demand entanglement distribution. Unlike traditional
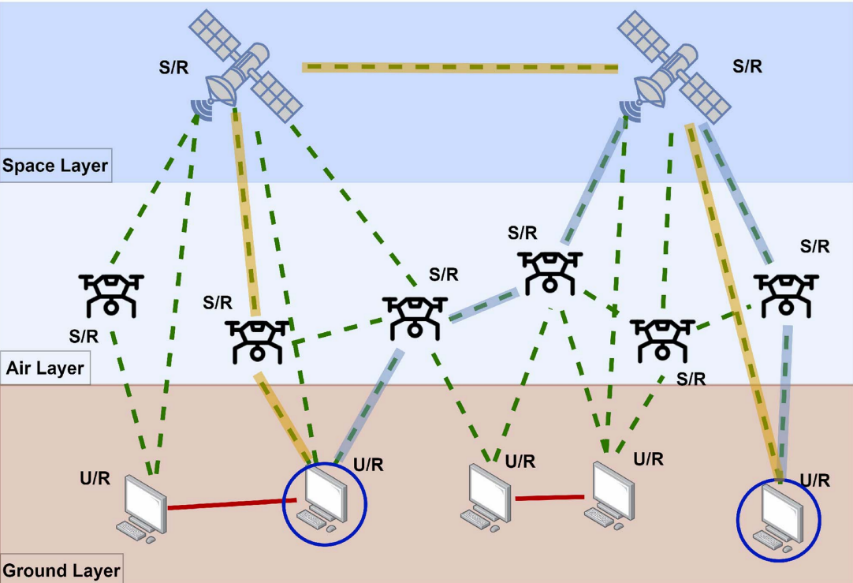 quantum networks that assume stationary ground nodes and homogeneous functionality,
SPARQ accommodates dynamic, heterogeneous nodes, posing unique routing challenges.
To address these challenges, we proposed a deep reinforcement learning (RL) framework
using deep Q-networks (DQN) for adaptive routing and introduced a third-party entanglement
distribution (TPED) policy. Our results demonstrated a 3% improvement in entanglement
fidelity and a 50% reduction in memory consumption. Additionally, our DQN-based routing
increased the number of resolved teleportation requests by 39% and improved entanglement
fidelity by up to 9% compared to state-of-the-art benchmarks.
quantum networks that assume stationary ground nodes and homogeneous functionality,
SPARQ accommodates dynamic, heterogeneous nodes, posing unique routing challenges.
To address these challenges, we proposed a deep reinforcement learning (RL) framework
using deep Q-networks (DQN) for adaptive routing and introduced a third-party entanglement
distribution (TPED) policy. Our results demonstrated a 3% improvement in entanglement
fidelity and a 50% reduction in memory consumption. Additionally, our DQN-based routing
increased the number of resolved teleportation requests by 39% and improved entanglement
fidelity by up to 9% compared to state-of-the-art benchmarks. - Efficient and Secure Entanglement Distribution in Hybrid Classical-Quantum Networks: To address the limitations of near-
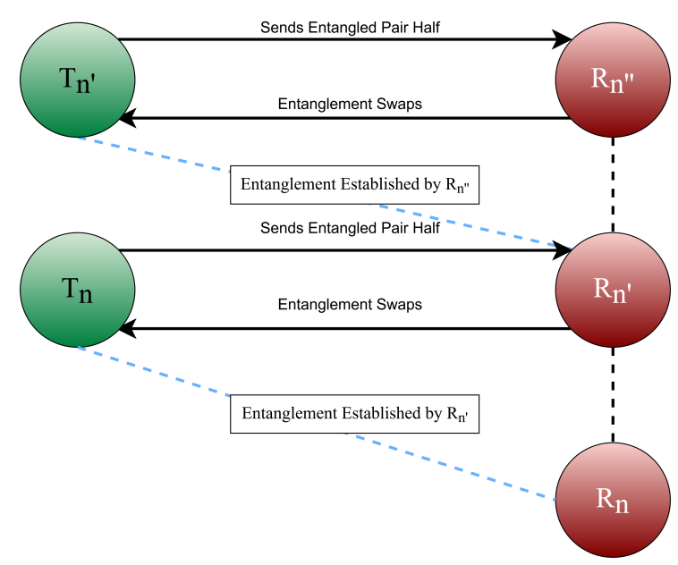 term quantum processors, we proposed an efficient entanglement distribution protocol
for hybrid classical-quantum networks with limited quantum links. Our protocol leverages
entanglement swapping and classical network coding to optimize resource usage, overcoming
bottlenecks while minimizing qubit and link consumption. Experimental results showed
that for small networks, the proposed protocol used 17% fewer qubit resources, improved
accuracy by 8.8%, and reduced simulation time by 35% compared to benchmarks, with
even greater improvements for larger networks. Additionally, we introduced a secure
entanglement distribution protocol using quantum state encoding through rotation,
reducing the probability of an attacker retrieving the teleported state to 7.2% without
adding communication overhead.
term quantum processors, we proposed an efficient entanglement distribution protocol
for hybrid classical-quantum networks with limited quantum links. Our protocol leverages
entanglement swapping and classical network coding to optimize resource usage, overcoming
bottlenecks while minimizing qubit and link consumption. Experimental results showed
that for small networks, the proposed protocol used 17% fewer qubit resources, improved
accuracy by 8.8%, and reduced simulation time by 35% compared to benchmarks, with
even greater improvements for larger networks. Additionally, we introduced a secure
entanglement distribution protocol using quantum state encoding through rotation,
reducing the probability of an attacker retrieving the teleported state to 7.2% without
adding communication overhead. - Designing a Regional Quantum Network in Tennessee (QNTN): We explored the feasibility of establishing a regional
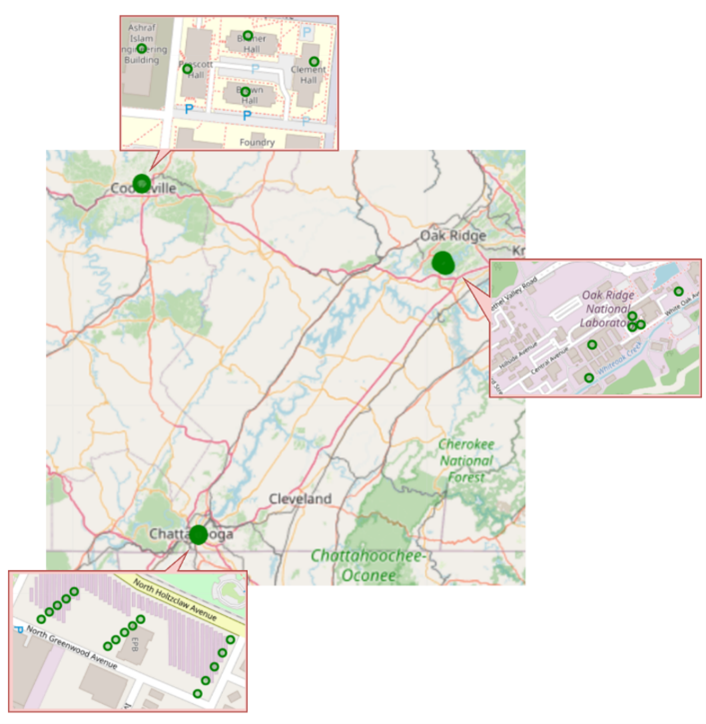 quantum network interconnecting three quantum local area networks across Tennessee.
Our study compared two architectures: a satellite-based space-ground model and an
aerial-layer model using high-altitude platforms (HAPs). While the satellite-based
approach achieved 55.17% daily coverage and handled 57.75% of entanglement distribution
requests with an average fidelity of 0.96, the HAP-based architecture provided full-day
coverage, fulfilled 100% of requests, and achieved a higher fidelity of 0.98. However,
operational limitations such as weather sensitivity and maintenance requirements pose
challenges for HAPs, highlighting the trade-offs between different network architectures.
quantum network interconnecting three quantum local area networks across Tennessee.
Our study compared two architectures: a satellite-based space-ground model and an
aerial-layer model using high-altitude platforms (HAPs). While the satellite-based
approach achieved 55.17% daily coverage and handled 57.75% of entanglement distribution
requests with an average fidelity of 0.96, the HAP-based architecture provided full-day
coverage, fulfilled 100% of requests, and achieved a higher fidelity of 0.98. However,
operational limitations such as weather sensitivity and maintenance requirements pose
challenges for HAPs, highlighting the trade-offs between different network architectures.
Our research at CEROC is driving the development of secure, scalable, and efficient quantum networks to support next-generation cybersecurity applications. By addressing the challenges of entanglement distribution and routing, we are laying the groundwork for a resilient and secure quantum Internet.
Applied Quantum Cryptography
With the rise of quantum computing, classical cryptographic systems face an imminent security threat. Quantum cryptography offers a solution by leveraging the principles of quantum mechanics to enable unconditionally secure communication. This field plays a crucial role in developing quantum key distribution (QKD) protocols, ensuring secure key exchange resistant to quantum attacks. Beyond QKD, quantum identity authentication (QIA) protocols provide a means to verify the legitimacy of communicating parties while preserving quantum security principles. Additionally, applied quantum cryptography contributes to secure multi-party computation, quantum-secure digital signatures, and post-quantum cryptographic integrations, all of which are critical for safeguarding next-generation communication networks, including 6G and the quantum Internet.
At CEROC, we are actively developing novel mechanisms to strengthen the security of quantum networks. Some of our recent contributions are:
- Quantum Identity Authentication Against Malicious Entanglements. As 6G networks evolve to support applications such as the metaverse, they require
robust security mechanisms to counter threats from quantum adversaries. While the
quantum
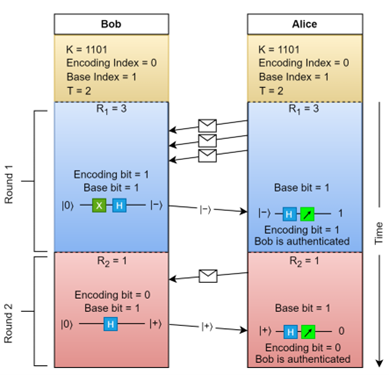 Internet enables highly secure communications through quantum entanglement, it also
introduces vulnerabilities, particularly when malicious quantum repeaters interfere
with entanglement distribution. In this work, we propose a quantum identity authentication
protocol designed to detect and mitigate malicious entanglements. Unlike existing
protocols that rely on periodic secret key refreshment, our approach eliminates this
requirement while maintaining strong security guarantees. Our simulation results show
that the proposed protocol can detect malicious entanglements with a 100% probability
after an average of just 4 authentication rounds. It reduces the number of authentication
rounds required to detect an attack by 69% and 76.5% compared to benchmark protocols.
By significantly enhancing efficiency and security in quantum authentication, our
research contributes to the development of trustworthy and attack-resilient quantum
networks, ensuring a secure foundation for future quantum-enabled applications.
Internet enables highly secure communications through quantum entanglement, it also
introduces vulnerabilities, particularly when malicious quantum repeaters interfere
with entanglement distribution. In this work, we propose a quantum identity authentication
protocol designed to detect and mitigate malicious entanglements. Unlike existing
protocols that rely on periodic secret key refreshment, our approach eliminates this
requirement while maintaining strong security guarantees. Our simulation results show
that the proposed protocol can detect malicious entanglements with a 100% probability
after an average of just 4 authentication rounds. It reduces the number of authentication
rounds required to detect an attack by 69% and 76.5% compared to benchmark protocols.
By significantly enhancing efficiency and security in quantum authentication, our
research contributes to the development of trustworthy and attack-resilient quantum
networks, ensuring a secure foundation for future quantum-enabled applications. - Access Control in Quantum Networks via Quantum Controlled Teleportation (QCT): Quantum Controlled Teleportation (QCT) is a fundamental technique for the quantum
Internet, enabling quantum information transfer under the supervision
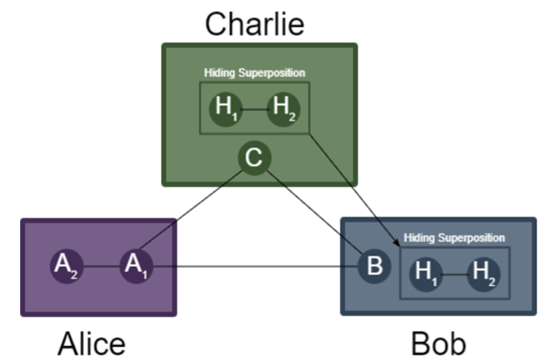 of a controller (e.g., Charlie), hence, providing access control in quantum networks.
Existing research has explored enhancing Charlie’s control level by improving the
fidelity of entanglement among communicating parties (Alice, Bob, and Charlie). In
this work, we propose a unified protocol that enhances Charlie's control level in
QCT networks, regardless of the entanglement technique or fidelity level. Our protocol
adopts quantum hiding techniques to strengthen security and control in quantum access
management. We analyze scenarios where Bob is compliant or non-compliant, demonstrating
the protocol's effectiveness. Our implementation via quantum circuits shows a 175%
increase in Charlie’s control level when applied to a low-fidelity entanglement technique
such as GHZ entanglement. Simulation results using IBM Quantum's QASM simulator confirm
a low reduction (2-7%) in successful teleportation rates, even in noisy environments.
of a controller (e.g., Charlie), hence, providing access control in quantum networks.
Existing research has explored enhancing Charlie’s control level by improving the
fidelity of entanglement among communicating parties (Alice, Bob, and Charlie). In
this work, we propose a unified protocol that enhances Charlie's control level in
QCT networks, regardless of the entanglement technique or fidelity level. Our protocol
adopts quantum hiding techniques to strengthen security and control in quantum access
management. We analyze scenarios where Bob is compliant or non-compliant, demonstrating
the protocol's effectiveness. Our implementation via quantum circuits shows a 175%
increase in Charlie’s control level when applied to a low-fidelity entanglement technique
such as GHZ entanglement. Simulation results using IBM Quantum's QASM simulator confirm
a low reduction (2-7%) in successful teleportation rates, even in noisy environments.
Upgrading the Classical Cyber Layer of Critical Infrastructures to Accommodate Quantum Cryptography Protocols
As cyber threats become more sophisticated, critical infrastructures such as power systems, financial networks, and transportation grids face an increasing need for quantum-secure cryptographic solutions. However, transitioning entirely to fully quantum key distribution (QKD) networks is costly and impractical due to hardware limitations. Semi-quantum key distribution (Semi-QKD) offers a practical alternative by allowing only a subset of nodes to have full quantum capabilities, while the rest operate with limited quantum functionality. This hybrid approach enables unconditionally secure key exchanges while minimizing infrastructure upgrades.
At CEROC, we have explored strategies for optimally upgrading the cyber layer of power systems to support Semi-QKD, ensuring the secure encryption and decryption of critical measurement and control data. Some of our key contributions include:
- Greedy-Based Quantum Server Allocation for Secure Key Distribution: In this work, we investigate how to upgrade the cyber layer of power systems to support semi-quantum key distribution while minimizing the number of required quantum servers (nodes with full quantum capabilities). We formulate an optimal quantum server placement problem to ensure that the required key distribution rate is met even in the presence of cyber-attacks. Due to computational complexity, we develop a greedy algorithm for quantum server allocation. Testing on the IEEE 14-bus system demonstrates that our approach effectively satisfies the required key rate under various attack scenarios.
- Genetic Algorithm-Based Optimization for Quantum Server and Fiber Link Allocation: Building on our prior work, this
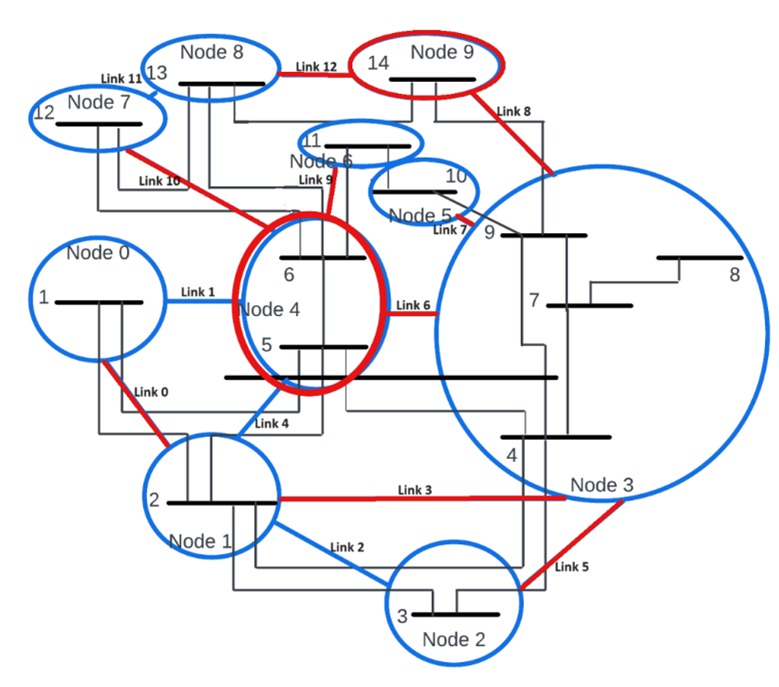 study extends the optimization problem to include both quantum server placement and
fiber link allocation. We formulate a binary optimization program to determine the
minimal required upgrades to support Semi-QKD. Given the complexity of the problem,
we design an optimal allocation strategy using a genetic algorithm. Testing on the
IEEE 14-bus and IEEE 39-bus systems, our results show: (i) A 33% and 67% reduction
in quantum server deployment for the IEEE 14-bus and 39-bus systems, respectively;
(ii) A 21% and 19% reduction in fiber link deployment compared to benchmarks; (iii)
A 52.17% and 54.65% reduction in overall infrastructure upgrades compared to standard
QKD deployment.
study extends the optimization problem to include both quantum server placement and
fiber link allocation. We formulate a binary optimization program to determine the
minimal required upgrades to support Semi-QKD. Given the complexity of the problem,
we design an optimal allocation strategy using a genetic algorithm. Testing on the
IEEE 14-bus and IEEE 39-bus systems, our results show: (i) A 33% and 67% reduction
in quantum server deployment for the IEEE 14-bus and 39-bus systems, respectively;
(ii) A 21% and 19% reduction in fiber link deployment compared to benchmarks; (iii)
A 52.17% and 54.65% reduction in overall infrastructure upgrades compared to standard
QKD deployment. - Optimizing Source Rates and Infrastructure Upgrades for Semi-QKD: Expanding upon previous findings, this work introduces an additional layer of optimization by considering optimal source rates for Semi-QKD. We refine our genetic algorithm-based strategy to minimize both quantum servers and fiber links while maintaining key rate requirements under attack scenarios. Our results indicate: (i) A 70% and 66.67% reduction in quantum server deployment for the IEEE 14-bus and 39-bus systems, respectively; (ii) A 31% and 17% reduction in fiber link deployment compared to benchmarks; (iii) An 80% and 97% reduction in required quantum server upgrades compared to full QKD implementation.
Quantum Machine Learning for Security Applications
Machine Learning (ML) and Artificial Intelligence (AI) techniques have become integral to modern security applications, including intrusion detection, malware classification, threat intelligence, and anomaly detection. As quantum computing advances, researchers are exploring its potential to enhance ML models for security applications, promising faster processing, improved pattern recognition, and higher resilience to adversarial attacks. However, the practical limits and vulnerabilities of Quantum Machine Learning (QML) remain underexplored, particularly in dynamic security environments where data distributions change over time—a phenomenon known as concept drift.
At CEROC, we have pioneered research on the effects of concept drift in QML models, assessing their resilience and adaptability compared to classical ML models. Some of our key contributions include:
- First Study on Concept Drift in Quantum Machine Learning: While quantum computing offers potential advancements in ML, the impact of concept drift in streaming data environments had not been explored before. We investigate the effects of concept drift on Quantum Support Vector Machines (QSVMs) and Quantum Neural Networks (QNNs), benchmarking them against their classical counterparts. Our study is based on two widely used streaming datasets: KDDCUP99 (a real-world cybersecurity dataset for intrusion detection) and RandomRBFDrift (a synthetic dataset with controlled drift patterns).
- Findings on Quantum Models' Susceptibility to Concept Drift: Our results reveal that quantum models are more
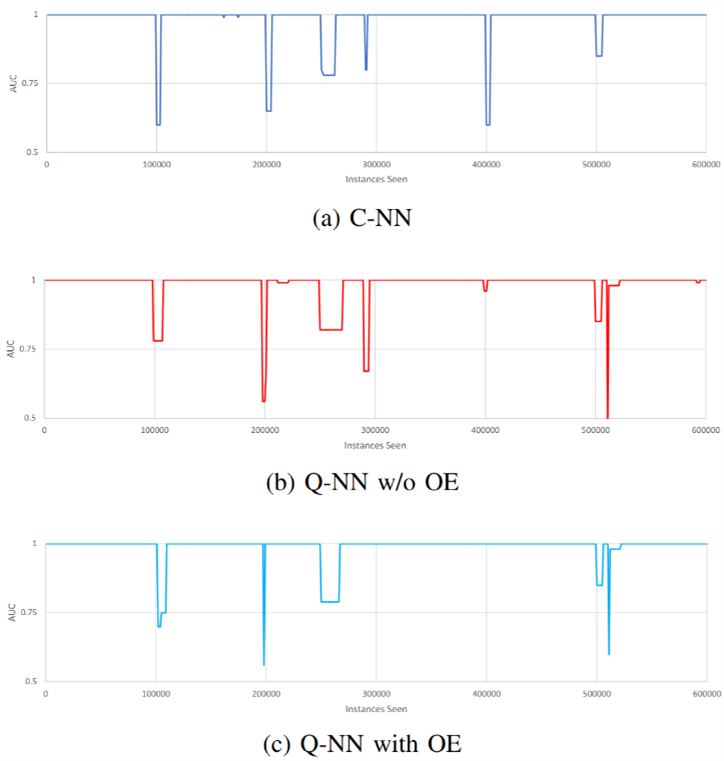 susceptible to concept drift than their classical counterparts when applied to the
KDDCUP99 dataset. This is evidenced by: (i) More severe drops in the prequential Area
Under the Curve (AUC) of the Receiver Operating Characteristics (ROC) curve; (ii)
Longer recovery durations for QML models after a drift event. Conversely, in the RandomRBFDrift
dataset, quantum models perform comparably to classical models, suggesting dataset-dependent
behavior.
susceptible to concept drift than their classical counterparts when applied to the
KDDCUP99 dataset. This is evidenced by: (i) More severe drops in the prequential Area
Under the Curve (AUC) of the Receiver Operating Characteristics (ROC) curve; (ii)
Longer recovery durations for QML models after a drift event. Conversely, in the RandomRBFDrift
dataset, quantum models perform comparably to classical models, suggesting dataset-dependent
behavior. - Mitigation Strategy – Optimized Quantum Encoding for Concept Drift: To counteract the effects of concept drift, we propose a genetic algorithm-based optimization strategy for encoding classical data into quantum states. Our approach dynamically selects: (i) Optimal encoding methods (angle, amplitude, basis encoding); (ii) Circuit depth and repetitions to balance expressiveness and stability; (iii) Adaptive quantum feature mappings tailored to dataset characteristics. Our results show that the proposed strategy improves model accuracy by up to 5% in the presence of concept drift, demonstrating enhanced adaptability of QML models in dynamic environments.
Our studies provide the first comprehensive insights into concept drift in quantum machine learning and opens the door for future research on robust, adaptive QML models for security applications. By understanding and mitigating these limitations, we move closer to harnessing the full potential of quantum computing for next-generation cybersecurity defenses.